Where does your personal data go after the trash?
My recently-found hobby of Dumpster Diving certainly brings me some very interesting things that people chuck away as some sort of "useless technology" that can be amusing or useful to me, or most of the time both. Aside from the technology items, sometimes there are also other interesting findings, like old music CDs and even pirated DVDs of varying quality.
There is, however, one worrying point that keeps showing up more and more in recent dives: personal data of previous owners discarded inside or alongside other pieces of "useless" technology and deemed lost or "unrecoverable" forever - that is, until someone else picked them up and realized they actually contained data.
When I first noticed this pattern, it seemed no more than just a small amusement for me. I'd laugh at the previous owners' carelessness of simply chucking thumb drives and SD cards away with not even remembering to delete the files first, and proceed to format the medium for my proper secure usage. However, as I kept finding more of these things carelessly discarded, it grew into a sort of collective worry for them, in the likes of "shoot, are these people seriously doing this?"
Rather than waste my energy worrying or trying to convince distracted users, I decided to put in this post some of the more extreme or alarming findings from my dumpster diving adventure, in addition to what we can do to protect ourselves from them.
Your toys have your PII
One of my recent findings from dumpster diving is an intact 2014-era Nintendo 3DS, a relatively rare find among the more usual broken screen or torn-apart ones that I find discarded in my area. But more interestingly, upon inspection it came with the SD card inside. Could it still be working?
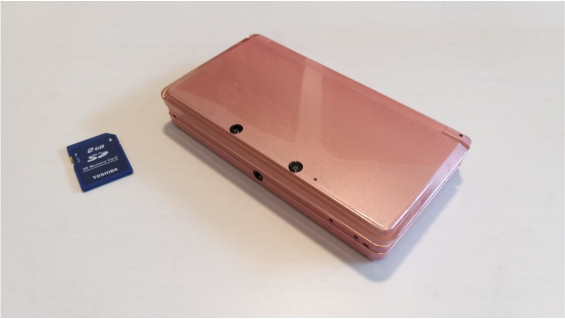
I thought about wiping it clean to sell it, but it turned out that the device itself was locked with some sort of parental controls from Nintendo that prevented me from factory resetting it. However, the wonderful hacker community once again surprised me when I found a very clever Master Unlock Code Generator from a guy who reverse-engineered Nintendo's algorithms. It worked perfectly and with that I had just "rooted" the device for myself. Small win for the day!
A larger treasure was the SD card still inside the device - could it still be usable? At 2GB in size it wouldn't be too useful for storage, but would definitely have its place as a boot medium for things like Puppy Linux. After setting up a live Linux session on my test machine without hard drives (malware could jump, I guess, and I have time to prepare the environment), I plugged in the SD and found out it was actually chock full of things - some of them very personally identifiable.
Most of the data stored were medium-resolution screenshots. I presume that, as part of the parental control mechanism, the DS took a screenshot of whatever game was running every 10 seconds or so, in a manner similar to the way Cellebrite, the software that once boasted it supposedly had "hacked Signal" works (unlike Cellebrite, though, I don't know whether these screenshots were transmitted over the network as well). I figure that this way, insecure and easily impressible parents could confiscate and "inspect" the DS at some unexpected time and know if their child was looking at porn from the DS's browser or playing a game not intended for their age range.
Whether this is efficient parenting is debatable (I think not), but it surely presents quite a lot of valuable identifiable information should the device end up on the wrong hands. For example, one of the games loaded on this DS is an AR Game that overlays "enemies" decorated with you and your friends' faces over the DS's camera feed from the place you're in. You can shoot these enemies and score points and walk around the area to get additional powerups. And coupled with the constant screeshooting function, one can have quite a detailed idea of how the child's house looks like from the inside, what their family looks like and who they spend time with.
Concerns over this sort of AR merging on top of real data are as old as Pokémon Go, and here we have another attack vector: the evidence is left unencrypted in the local storage. No forensics needed - lovely.
Next, we have the terrible but ridiculously overdone idea of the internal-facing built-in camera of the 3DS. I mean, we aren't spied enough yet in our daily life, so we should add yet another camera facing us up close, right? And as most children these days are being taught to do, there were the selfies. Alone, with friends, at home, at places - more PII being leaked around. Not much of a problem if it's only local storage and it's being shared with only your trusted friends, but a larger threat should these fall in unintended hands. And as we just saw, there's a small chance that when you throw it in the trash without formatting, someone curious could still pick it up.


How much identifiable stuff can fit in such a tiny thing?
Next up is a USB drive I also salvaged from the trash. It's really tiny in size, with the storage "head" being about 0.5mm not counting the USB connector itself. Yet, this one was a real treasure - 32 GB of storage in apparently good condition.

Likewise the DS, I guess the previous owner didn't think anyone else could find it - even I had trouble identifying it along the mountain of trash it was in - and threw the device without formatting or encrypting it. I'm guessing he was a middle-aged small business owner from the contents of it since, instead of pirated MP3s, what I found was his plans to staff and operate a business:
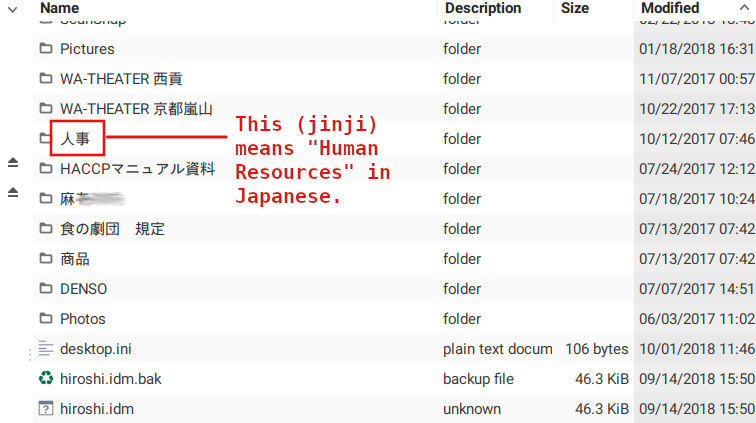
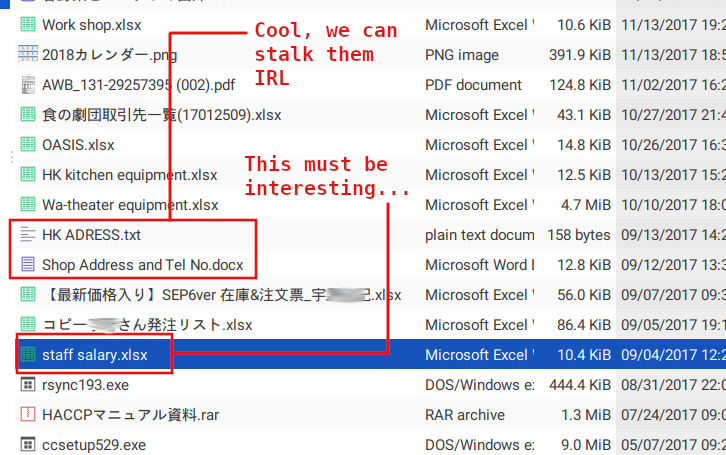
This goes to show that sometimes, however much you try to safeguard your own information, it ends up in the hands of someone who is careless and doesn't treat it securely enough. Yes, I'm looking at you, online services. And if this person backed up these contents into some sort of "cloud" storage, then my possession of this information is really the least of his privacy concerns.
Not even your phone?
Last but not least, we have the case of someone who dumped a perfectly-working smartphone in the trash as "broken" presumably because the screen cracked. There was no SD card in it this time, but that didn't protect the internal storage. And for some spectacularly dumb reason, this phone's firmware actually allows anyone to view the pictures taken from it - even if the screen is locked and you don't have the password.




Unbelievable. I think this sort of developer irresponsibility really takes the cake for privacy failure. I didn't even bother accessing the phone's content from my computer after this low-hanging fruit.
Appendix: What can you do to protect yourself?
Needless to say, I wiped all the aforementioned storage devices clean and encrypted them for my own use. I want no data from these previous owners, and the less I know about them the better.
First off: encryption is a must if privacy is desired. The two go hand-in-hand and there's no realistic expectation of privacy and security without end-to-end encryption. And the best part: it's easy to do! If you install gnome-disk-utility in any modern distro (including Alpine), you get nice and easy GUI that can format and encrypt the volume as easily as using a wizard.
There's only one downside: the volume becomes readable only on Linux. I don't consider that a bug though, but rather a feature.
Disk encryption not only ensures the confidentiality of the data during transportation, it also ensures that if you lose it, or would like to discard the medium, anything it holds is basically unreadable to anyone without your password. However, if you haven't done so, you should securely wipe off any data that the medium holds before discarding it. And no, pressing Ctrl+A and Del from a graphical file manager doesn't count.
There are multiple ways of accomplishing this on Linux, dd if=/dev/zero of=/dev/sdX bs=1k count=4096 being one of them, and even the simple mkfs.vfat /dev/sdX usually sufficing. Most of the times, there's no need to DBAN it completely. A fair warning, though: due to the way that SSDs and some flash media behave to "reduce wear," even this might not delete 100% securely the contents of the drive. A very motivated adversary could still use forensic recovery options to analyze the content. Most casual adversaries, like almost all dumpster divers, though, will consider it lost.
Finally, another lesson that remains is: use software that respects you. Would you live in a house that randomly opened up the window blinders without your consent to let outsiders peek in? Or own a car that would unlock itself for any stranger to get in and see what's inside of it? Because that's the sort of vibe that I get from OSes shown in the phone and the DS of this post. Using a Free Software operating system can be a good, if not the best, way to ensure that your privacy is protected.
Digital self-defense is a must for everyone. To think that security is something that can be outsourced completely today is carelessness at best, but, as my experience dumpster diving has shown, unfortunately a concept still widespread among computer users.
Have you ever uncovered PII from some unsuspecting piece of technology deemed lost forever? What would you recommend that people do before discarding their Tech? Let me know on Mastodon!
Note: kzimmermann is a strong personal privacy advocate and will never disclose anyone's personal information in a vulnerable manner for any reason whatsoever. All the examples shown here were carefully and responsibly redacted, and the original data destroyed with no possibility of recovery. All the storage media is now owned by me and encrypted with LUKS, with no possibility of me accessing the original owners' files.
This post is number #19 of my #100DaysToOffload project. Follow my progress through Mastodon!
Last updated on 06/12/21